
The Downfall of REvil
December 13, 2021
Topics
- Ransomware

December 13, 2021
Topics
REvil, also known as Sodinokibi, is one of the most notorious ransomware gangs in the cyber crime era. They are a Russian based Ransomware-as-a-Service (RaaS) group that has many followers in the DarkWeb community. They practice the double extortion technique where they encrypt victims’ data and then threaten to release the data on their “Happy Blog” web page for the public to see if the ransom is not paid. REvil is known for many high-profile cases including the Acer attack, the ransom of Apple’s supplier Quanta Computer, the attack on the United States meat company JBS, and the hack of Kaseya. However, their high-profile cyber attacks had put the gang in the priority list of many law enforcement agencies, and in recent news it seems REvil servers has been compromised by law enforcement and members have been arrested.
In July 2021, after their attack on Kaseya, REvil’s Happy Blog leak site went offline. According to them, they shutdown due to immense pressure from law enforcement agencies. A couple of weeks later, the site was back online and REvil was back to their ransomware activities. However, during this time, news of the FBI obtaining and withholding ransom decryption keys for the Kaseya attack surfaced. The FBI had refrained for almost three weeks to aid companies affected by the Kaseya ransomware in order to conduct operations aimed at REvil. While many did not believe this, a representative from LockBit posted on the DarkWeb forum .XSS a different perspective. The LockBit representative believes that the FBI was able to gain access to the decryption key by gaining access to REvil servers. However, to gain access to REvil servers the FBI will need to obtain access keys who only REvil members should have. Thus, the LockBit gang strongly believed a high-ranking member of REvil gave their access key to the FBI. In October of 2021, REvil’s servers were shutdown and it is revealed that law enforcement and intelligence agencies from multiple countries had hacked REvil’s servers and backups.
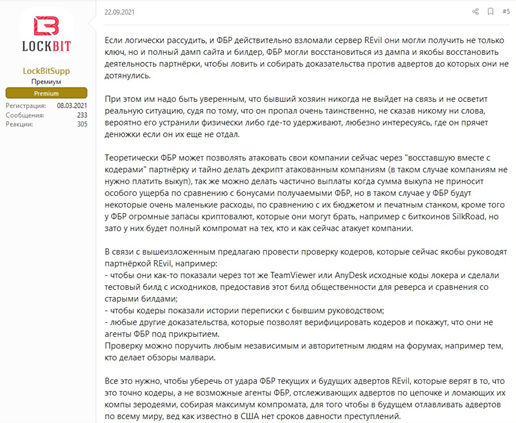
After the July 2021 shutdown, REvil operators believed that one of their key members, “Unknown”, had disappeared. Some believed that the spokesperson had died. But then, somebody used Unknown’s access keys. After the October shutdown, the REvil members stated that the REvil domain was accessed using Unknown’s keys, confirming their concerns that a third-party has backups with their service keys.
When the other members of REvil restored their website from a backup in September, they unknowingly restarted some internal systems that were already controlled by law enforcement. Using this opportunity, law enforcement agencies began to hunt for REvil members and affiliates. Although REvil shutdown in October, law enforcement agencies were able to arrest affiliate members. In November, it has been reported that law enforcement agencies worldwide have arrested five members tied to the REvil Ransomware Gang, plus two more affiliate members. The FBI was also able to seize $2.3 million USD from REvil, which is about 39.89138522 bitcoins.
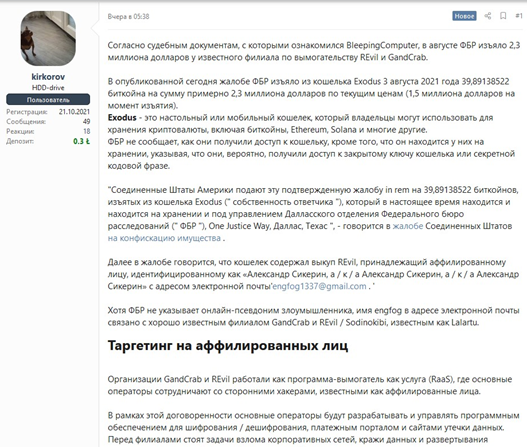
When REvil shutdown for the second time in October, many in the DarkWeb community believed the group will return, possibly rebranding themselves. However, when news law enforcement agencies seizing millions of dollars and arresting REvil members and affiliate members, many started to believe that this was the end of REvil. The Groove Ransomware gang even proposed to the ransomware community to gather and start attacking the United States in revenge for REvil. In the end, this may truly be the end of the REvil group, however, many other ransomware gangs will take their spot. Ransomware groups such as LockBit, now the biggest group, and Conti, on the rise with the revival of Emotet malware, are gaining former REvil affiliates. When the fall of one of the biggest ransomware gangs, it is clear that world governments are attempting to bring down ransomware activities. Hopefully, this is the beginning of government agencies’ counter attack to ransomware activities.