
Job Hunt or Data Hunt? The Rise of Malicious Recruiters in Cyberspace
October 12, 2023
Topics
- advanced persistent threat
- Social Engineering

October 12, 2023
Topics
Hackers, whether they are working by themselves or part of a larger APT (advanced persistence threat) group, are constantly thinking about new ways to launch attacks against individuals and organizations around the world. Most of these hackers and APT groups share common motives ranging from things like revenge and hacktivism to financial gain. Things get a little more complicated when hackers are working on behalf of a state-sponsored operation, especially when that state is North Korea. Recently, there have been reports of hackers connected to the North Korean state posing as job recruiters to deploy complex malware onto the devices of individuals around the world.
APT38, Gods Apostles, Gods Disciples, Guardians of Peace, ZINC, Whois Team, and Hidden Cobra are all names that have been associated with the hacking conglomerate that we now refer to as Lazarus. Lazarus is a North Korean state-sponsored hacking operation that has been active since as far back as 2009. They are known for their espionage campaigns and attacks against banks and other financial institutions. One reason that North Korea might be backing a hacking group is to gain information and funding for its nuclear program. Some information that the Lazarus group can gather is thought to be used by their nuclear program. Experts also suspect that a sizeable portion of money stolen by Lazarus is used to fund a portion of North Korea’s growing nuclear operation. Some of their most famous cyber-attacks include the 2014 hack against Sony Pictures and the 2016 heist on the Central Bank of Bangladesh where they stole $81 million.
Throughout 2023, there has been a steady uptick in malware distribution campaigns involving fake job recruiters. The entire operation involving fake job recruiters deploying malware has been titled “Operation Dream Job” as it involves fooling working with lucrative job opportunities. Earlier this year in March, a campaign targeted towards Linux users was launched using fake HSBC job offers that were used to install a backdoor trojan known as SimplexTea.
In the latest reports of this malware campaign users have found themselves being contacted on LinkedIn and other job search websites by recruiters at prominent technology companies. Such cases involved an employee from a Spanish Aerospace firm being contacted by a recruiter at Meta. The hacker tricked the employee into opening a malicious executable, disguised as a coding challenge, on a work laptop. Once the executable was opened, it started the download of multiple malicious packages with the end goal of deploying NickelLoader. NickelLoader is an HTTPS downloader that allows the attacker to download any program directly into the memory of the computer. Once NickelLoader was deployed it was used to launch LightlessCan which is used for harvesting and transmitting data. Since all of this was done on the employee’s laptop, it led to the eventual compromise of the system and breach of the corporate network.
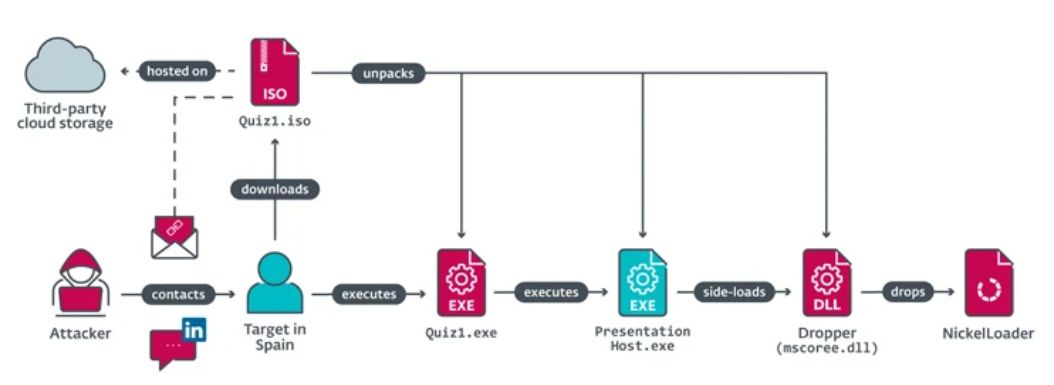
The targeting of an aerospace firm falls in line with the known motives of the Lazarus group. In this case, it was not monetary gain they were after, instead, it was knowledge. It can be assumed that they chose to target this specific company in hopes of acquiring information that could be used in some of their nuclear technologies.
The infamous Lazarus group has once again made headlines. However, this time they used a tactic that many people may not have expected. The use of fake job recruitment scams is not unheard of. In the past, this scam was used through fake job boards. In the most recent iteration of this campaign, hackers are selectively targeting employees of specific firms in hopes of gaining confidential information.
There are a few steps that can be taken to protect yourself and your organization from these malicious campaigns. The first step would be to implement a policy that can be pushed to the whole enterprise which blocks the download of executable files without authorization of an administrator. Another route you can choose is implementing endpoint protection that scans files and blocks them if they are malicious. You can also set up web filtering to prevent employees from navigating to websites such as LinkedIn and other job boards while connected to the corporate network. Any of the above steps alone or in combination with the others are simple measures that can be taken to help reduce the chance of your organization becoming the next victim of this malware campaign.
https://thehackernews.com/2023/04/lazarus-group-adds-linux-malware-to.html
https://therecord.media/north-korean-govt-hackers-spain
https://www.cyberpolicy.com/cybersecurity-education/who-is-lazarus-north-koreas-newest-cybercrime-collective
https://attack.mitre.org/campaigns/C0022/