
Lapsus$
April 1, 2022
Topics
- Malware
- Ransomware
- campaign

April 1, 2022
Topics
The Lapsus$ ransomware gang has recently gained immense notoriety due to their attacks on major corporations such as Microsoft, Samsung, Nvidia, and most recently Okta. Lapsus$ first made themselves known back in January 2022 when they pulled off cybercrimes that seem more in line with pranks than for financial gains. For example, in one of their first hacks of the year the gang attacked a Brazilian car rental company, redirecting the business’ homepage to a porn website for several hours.
Lapsus$ has taken the responsibility for the attacks on major corporations and has proved that they have gained some of the source code to some of the targets’ products. Gaining source code to Nvidia, Samsung, and Microsoft will most likely cause a severe supply chain reaction, which can lead to multiple organizations and machines being infected and harmed as both, Nvidia’s, Microsoft’s, and Samsung’s firmware and hardware are used globally. Using the source code threat actors can bypass security technologies, by adding stolen certificates that are signed and verified as legitimate as part of their malware.
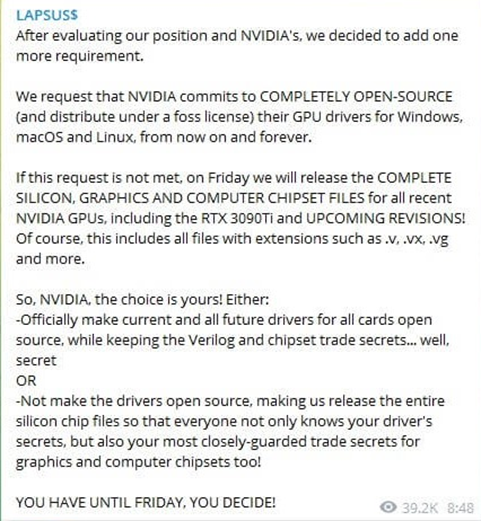
An area of strength of the Lapsus$ group is their intrusion techniques. The group does not use any sophisticated techniques to get inside networks and systems, instead, they leverage well-known strategies that include the use of a credential stealer malware called “Redline”, social engineering tactics, and the purchase of stolen passwords and session tokens on the DarkWeb. The group also frequently attempts to hire insiders from target companies. In one case, the group offered employees at Verizon and AT&T as much as $20,000 a week to aid in the criminal operation.
While Lapsus$ has gained infamy through its attacks on major corporations, users of on the DarkWeb forums have been exposing the group, especially on one of its members. On the Russian DarkWeb forum “.XSS”, a threat actor under alias “UnknownDeath” created a thread trouncing on one of the Lapsus$ members.
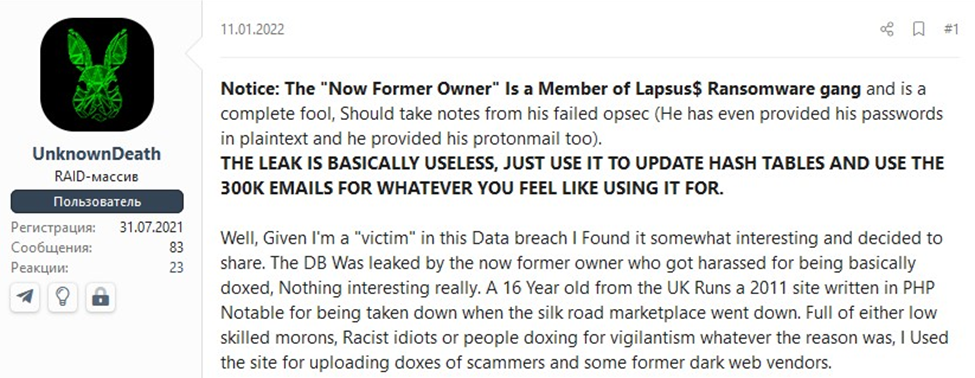
From Perimeter Watch Threat Intelligence Team’s investigation, UnknownDeath is talking about the database of DoxBin. DoxBin is a community website where hackers “dox” anyone they want, but mostly aimed towards other threat actors or hackers. Doxing is a term used to publish private or identifying information about a specific individual on the internet, mostly for malicious intent. Apparently, one of the members of Lapsus$, under the alias of “White”, was a former owner of the DoxBin website, but because of White’s mismanagement the website began to lose popularity. Before selling DoxBin back to its original owners, White released the database of DoxBin users out of spite. Doing so, White became public enemy number one amongst the members of DoxBin. The currently owner of DoxBin has published a dox of White, with information including name, emails, passwords, family members, etc.
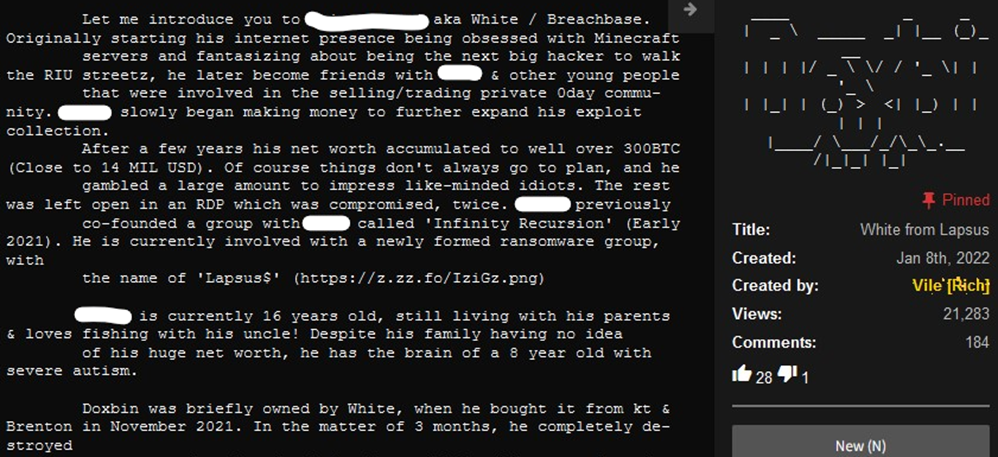
Evidence shows that the Lapsus$ group may not be seasoned hackers. Instead, the group may be a group of teenagers ranging from ages 16 to 21. One evidence is the doxing of White, a member of Lapsus$. In the dox, it is mentioned that White is a 16-year-old teenager from the United Kingdom. Also evident is the organization and activity of the Lapsus$ group. Unlike most ransomware gangs who uses a shame blog website to post stolen data, Lapsus$ post all their activity and leaks on their Telegram Channel. They announce their target and then shares leaks almost immediately once they exfiltrate the data, thus, giving no time for their victim’s to even pay a ransom. This behavior indicates that the group’s goal may not be financial, instead, they are doing this for the thrill, which illustrates how young the threat actors are. Many cyber security researchers also believe the gang is formed by a group of teenagers. In fact, it is currently believed that the leader of the group is White, the 16-year-old from the United Kingdom. If true, it would make sense considering the dysfunction of the group is like White’s mismanagement of DoxBin. Considering he was easily doxed by his adversaries, White’s security operations (SecOp) has been relatively poor and that has trickled down to Lapsus$ SecOps, which has been continuously mentioned as “garbage” by users on the DarkWeb forums. Lapsus$ poor SecOps has led to a recent arrest in London of seven of their members, however, it is currently unclear if they are indeed related to Lapsus$ as the group has posted in their Telegram channel that the arrests of seven teenagers have no relation to them.
Conclusion
The Lapsus$ gang has performed flashy attacks and has gained tremendous notoriety. They have unorthodox techniques, and their modus operandi appears to be creating chaos and hacking for the thrill, instead of financial gains. The group has shown levels of immaturity, which leads many to truly believe that the gang is a group of teenagers being led by a 16-year-old under the alias, White.
To avoid possible attacks from the Lapsus$ gang, here are some suggestions: