The threat actors were able to infiltrate the analyst’s computer for almost a year. The hackers dumped the contents of the analyst’s mailbox, as well as several internal Mandiant and FireEye documents. The dump was a treasure trove of highly sensitive internal information that included, network topologies, threat intelligence profiles for the Israeli Defense Forces, and company worksheets, however, most of the leaked data focused on the analyst. Shortly after the attack, the alleged hacker was arrested in July 2017. Although the hacking group appears to have returned, there is no indication that it is the same hacker from 2017.
DarkWeb Intelligence
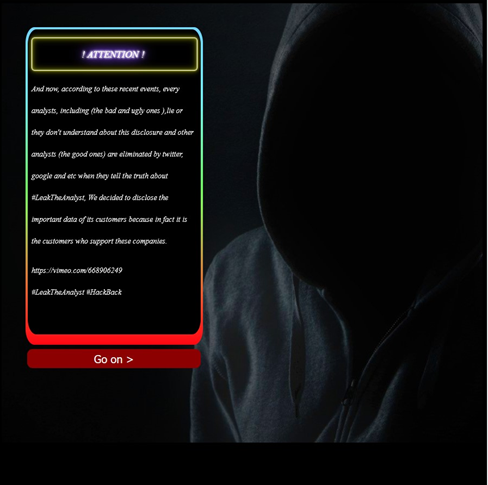
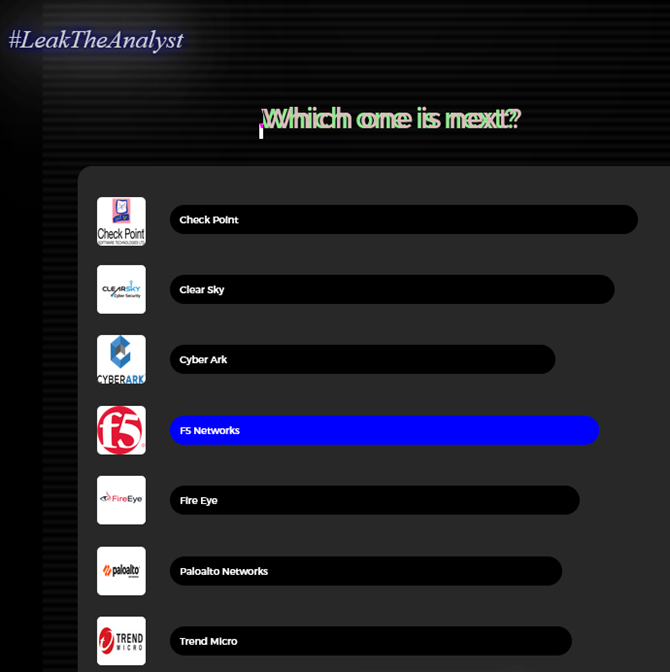
Perimeter Watch’s Threat Intelligence Team was able to find a thread on the Russian Forum .XSS, where threat actor under the alias “4ndtips” shared about the return of the LeakTheAnalyst group. According to the thread, some are anxious to see who the group is going to target, while others believe it to be a hoax. The Threat Intelligence Team was able to find a link to the threat actors’ website and investigated further. The first thing we see was a video created by the group that signified their return and agenda. Next, was a page where visitors of the website can vote for the group’s next target, which includes security companies such as Checkpoint, Cyber Ark, FireEye, PaloAlto. The voting seems to have pointed towards F5 Networks, a technology company.
Threat Analysis
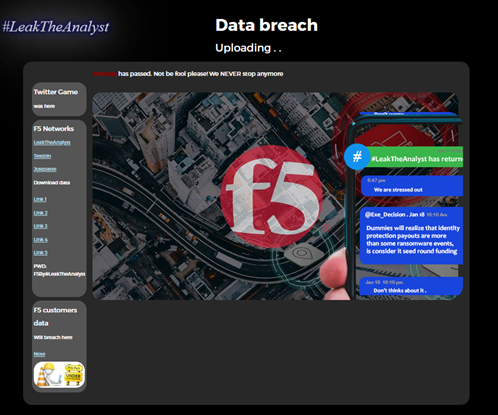
If the group truly has returned then security companies need to be aware of this potential threat, as the hacking group aims to target employees of these companies. According to the website, they will leak their next victim’s data on Monday, January 24, 2022. On another page titled “Data Breach”, the group has posted links to download data supposedly leaked from F5 Networks and they appear to be uploading more data that may include F5 Network’s customer data.
Conclusion
While it is uncertain if the return of LeakTheAnalyst is true or a hoax, security researchers and analyst will be keeping a close eye on this threat acting group. The group proves to be highly skilled hackers as they were able to infiltrate a cyber security’s employee’s computer and avoid detection for at least a year. While that incident was 5 years ago, the threat actors will surely have improved their skills and learned from their past mistakes.