
A Switch From the Norm - A New Malware Infection Chain
May 3, 2022
Topics
- malware analysis
- phishing campaign

May 3, 2022
Topics
Let’s have a look at a common infection vector that persists through the use of excel based macros.
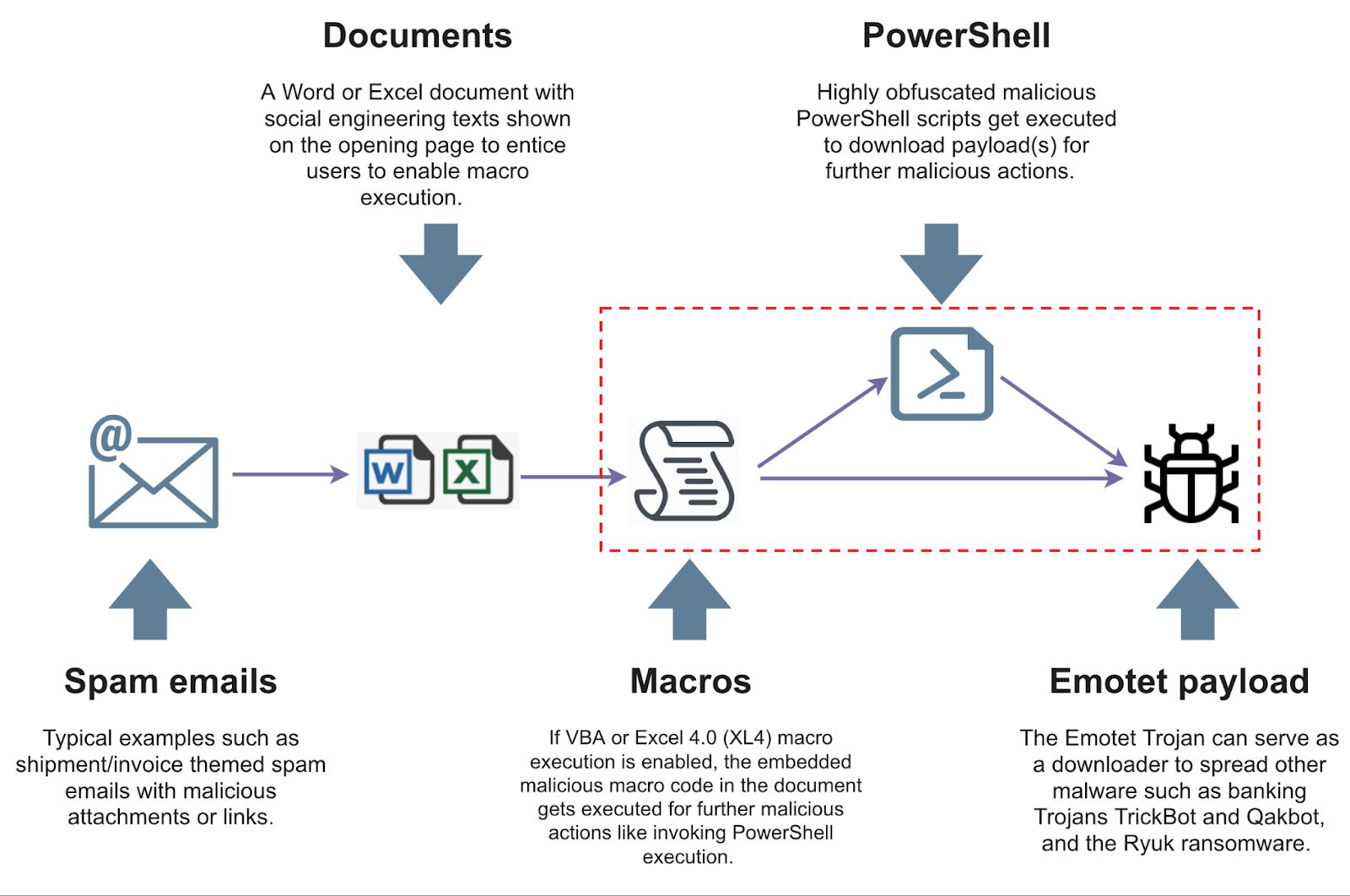
Here we see an excel sheet downloaded from an email. Upon opening the excel sheet, a user gets asked to enable macros if the macros were disabled by default. If macros were not disabled, the macros would automatically run, executing their malicious code. The next step involves the malicious code executing a trusted program such as PowerShell, which will download more dangerous malware from the internet.
What is important here is that if macros are not automatically disabled, this process will happen the moment the document opens. With Microsoft disabling macros by default, it now leads malware authors to utilize a different infection chain.
On April 11, 2022, the Qbot botnet was reported to have transitioned to sending phishing emails attached with password-protected ZIP (PPZ) archives that contained MSI Windows Installer Packages. Researchers believe this is a direct reaction to Windows disabling Excel 4.0 macros by default. This different method of infection vector presents new problems for security vendors and companies in relation to the enforced email policy.
PPZ files are encrypted, making it so that antiviruses cannot scan what is within them. If a password-protected zip file is sent over an email, simple signature scans would be ineffective in stopping these attacks. Therefore, a method to prevent this infection vector would be to block password-protected zip archives.
While blocking PPZ files is effective in stopping this infection vector, this can lead to many false positives. PPZ files are frequently used for a company to transmit sensitive and confidential information over an internal network and would not make sense for larger organizations that use this policy.
When making a policy, it is essential to tailor it to the client. Therefore, we ask clients to implement policies that allow their documents to be scanned after being downloaded onto their workstation. If left unmanaged, this can lead to hazardous computer infections. These documents should be run in a controlled and sandboxed environment before being allowed to run on the current system.
If this cannot be allowed, another method is the usage of digital certificates to encrypt and verify the sender of the document. This approach will remove the need for a password-protected document and determine who sent the document and if that source can be trusted.
More info is still needed to know if other malware botnets will follow this trend. The use of PPZ files containing MSI executables is still new. Researchers and defenders should be made aware of the change in tactics in the coming months and change their policy accordingly to tailor their clients' needs.