
Unraveling The Decoy Dog Malware
August 7, 2023
Topics
- Malware

August 7, 2023
Topics
Researchers at Infoblox discovered a new RAT (remote access trojan) toolkit in April of 2023. This new strain of malware is known as Decoy Dog. Soon after its discovery, Infoblox disclosed all the information that it had on the malware at the time. After learning that news of the RAT had become public, the operators of Decoy Dog quickly adapted the malware to continue pursuing on devices. Now, Decoy Dog has once again made headlines due to it being reported that the RAT has evolved and gained additional features.
The newly discovered RAT known as Decoy Dog is based on the pre-existing open-source RAT known as Pupy. Pupy is widely available on the internet through hacking forums, the dark web, and even on GitHub. Due to its open-source nature, it makes traditional methods of detection difficult. Anyone or any organization can alter the source code however they would like to change or add things specific to their goal.
This trojan is most commonly spread through spear phishing emails. These emails contain macro-enabled files that, when run, execute a PowerShell command that initiates the download of the RAT. Once this malware has been installed on the target device, it gives the attacker full control of the system.
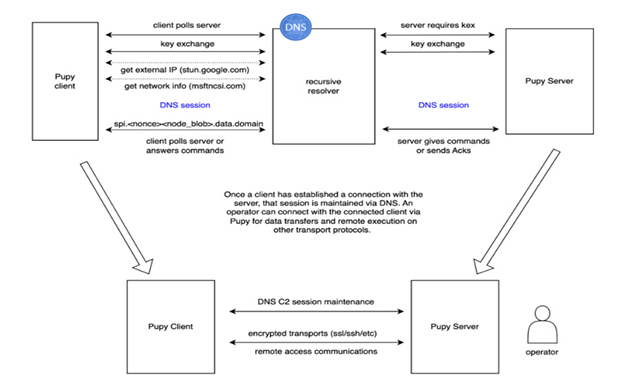
Decoy Dog is a RAT toolkit that utilizes DNS to perform C2 (command and control). This toolkit was discovered by Infoblox in April 2023 using anomaly algorithms built into their BloxOne Threat Defense resolvers. Through research, they discovered that this toolkit is based on Pupy. However, this RAT is much more advanced than Pupy. Some of the key differences between the two are new command and communications protocols, being able to avoid disruption of communication between client and server, and different core communications modules.
Although the trojan was first discovered in April of 2023, reports have shown that this malware has been active from late March to early April of 2022. Currently, Decoy Dog has accumulated a total of 21 controller domains with more on the way. On top of that, the Decoy Dog operation has also expanded from 1 threat actor when it was first discovered, to at least three threat actors now.
Through the ongoing research that has been conducted, a key piece of information has come to light. Many of the domains that act as the servers for Decoy Dog are registered to Russian IP addresses. This has led many people to believe that this is a state-sponsored operation. However, another thing to note is that there have not been any reported attacks involving Decoy Dog. Researchers are estimating that there are over 100 devices that are infected with this RAT but have not yet discovered it.
Since there have been no reported attacks involving Decoy Dog, it is still unknown how this RAT spreads, and who are the threat actors behind this malware.
The best way to protect your organization against the Decoy Dog malware is through DNS detection and response. Malicious activity in many cases goes unnoticed due to improper DNS configurations. It is recommended that you use DNS to block access to malicious resources regardless of the OS or application being attacked. Another step you can take is actively reviewing DNS logs for anything that looks suspicious.
Another step that can be taken is the implementation of YARA rules. Researchers at Infoblox have published a YARA rule onto their Github repository that detects Decoy Dog. Implementing a rule such as this one or even modifying this rule to be more fine-tuned to your environment could prove to be beneficial when dealing with the RAT.
Decoy Dog is a highly dangerous malware due to its long-term persistence tactics. Although there are still many unknowns surrounding its origins and ultimate purpose, it can be said that for the time being its goals are long-term persistence and data gathering. As time goes on, researchers will undoubtedly uncover more information about how this malware is spread and even greater details about how it operates, but until then we must take any measures available to protect our organizations.