
Vice Society
November 7, 2022
Topics
- advanced persistent threat

November 7, 2022
Topics
Over the past couple of years, there has been an increase in remote learning and virtual classrooms for schools due to the coronavirus pandemic. However, this major shift to distance learning provided new opportunities for the education sector to be the frequent targets of ransomware attacks. With ransomware attacks on the rise, multiple security teams have identified a ransomware group named Vice Society and their attack campaigns against the education sector.

Vice Society is a ransomware group that initially appeared in June 2021. Although the group has been active since then, Vice Society was able to maintain its low profile until now by targeting small-sized schools. What makes Vice Society unique is that it targets organizations that have weaker security controls due to a lack of resources and exploit them for a ransom.
The group typically carries out its initial phase of the attack chain by exploiting web-facing application vulnerabilities. Once they gain a foothold in the system, they explore their victim’s network by utilizing several post-exploitation tools including Powershell-Empire and Cobalt Strike. The group was also seen using a tool called Impacket, a suite of scripts written in python that can offer network protocol communication and vulnerability-scanning applications. It’s highly likely that the group relies on this tool heavily during intrusion in order to enumerate the victim’s environment and identify high-value targets.
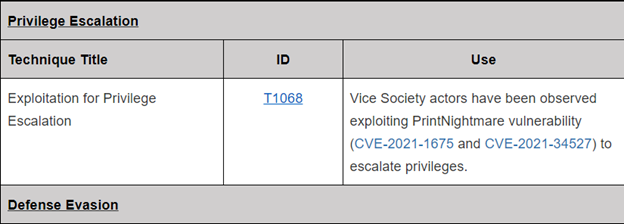
According to CISA, Vice Society threat actors then continue to further their attack chain and escalate privileges by exploiting PrintNightmare vulnerabilities (CVE-2021-1675 and CVE-2021-34527). While Vice Society doesn’t focus on developing its own tools, it has been observed using multiple commodity ransomware payloads such as HelloKitty and Zeppelin ransomware. Additionally, it’s been reported by Microsoft Threat Intelligence Team that the group has recently incorporated their own branding into the ransomware payloads with file extensions using .v-s0ciety or v-society. The use of multiple malware strains has led many security experts to believe that the group has now gained an ability to modify some of these commodity ransomware payloads. One finding that has been interesting about Vice Society is that the strain of Zeppelin they use does not match any previous strain of the malware. It has been hypothesized that Vice Society has been able to manufacture or get their hands on a custom variant of this malware to use for their operations.
In one of their recent attacks, the group targeted Los Angeles Unified School District (LAUSD), the second largest school district in the United States. It is believed that the timing of the attack was carefully planned out and carried out over Labor Day just when most of the schools re-open for the year. Security experts are convinced that the group chose this day to pressure the schools in an attempt to increase the likelihood of ransom payment. The group eventually posted stolen data on their site when the district refused to pay a ransom. In one of the posts on their site, Vice Society also left a message, “CISA wasted our time, we waste CISA reputation” with the assumption that the CISA played a critical role in interfering with the release of the stolen data by Vice Society.
A lot of mystery surrounds this organization as there has not yet been enough research or evidence towards uncovering the identity of Vice Society threat actors. Although the group has been under the radar, many organizations are starting to pay more attention to the threat actors whose purpose is to target schools for financial gain. Additionally, the group’s ability to manufacture a custom strain of the Zeppelin ransomware has made security experts to begin questioning what kinds of connections Vice Society has in the cybercriminal world. In the coming months, it will be interesting to see if the group continues to target educational institutions or begins to shift towards even more mainstream targets.