
Yanluowang Ransomware
December 3, 2021
Topics
- Ransomware

December 3, 2021
Topics
A new ransomware strain was discovered by researchers at Symantec while responding to a recent attack against a large organization in October. The Symantec team first spotted suspicious use of AdFind on the victim organization’s network. AdFind is a legitimate command-line query tool for Active Directory but often abused by ransomware attackers as a reconnaissance tool, as well as to equip the attackers with the resources that they need for lateral movement via Active Directory. Just days after the suspicious AdFind activity was observed on the victim organization, the attackers attempted to deploy the Yanluowang ransomware.
Before the ransomware is deployed, a script is used to carry out the following actions:
• Creates a .txt file with the number of remote machines found on the network
• Uses WMI (Windows Management Instrumentation) to create a text file of current processes running on the remote devices found in the previous .txt file.
• Logs all processes and remote machines found to a text file named “processes.txt”
When this process finishes, the Yanluowang ransomware is deployed, and the following actions take place:
• Stops all hypervisor virtual machines running on the compromised computer.
• Ends all processes that were listed in the “processes.txt” file created earlier.
• Encrypts files on the compromised computer and appends each file with the. yanluowang extension.
• Finishes the process by dropping a note named README.txt on the victim machine.
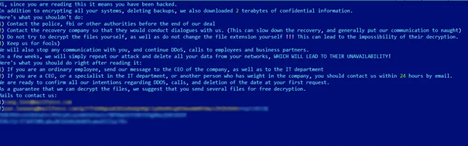
Researchers found a “tentative link” between the new Yanluowang attacks and older attacks involving Thieflock, a ransomware-as-a-service (RaaS) originally developed by the FiveHands group. Ransomware authors and affiliates are known to pivot often, usually searching for the highest profit margins offered or the least amount of attention from law enforcement. Symantec’s Threat Hunter Team noticed several TTP’s used by Thieflock that seem to link them to this new ransomware. These include:
• Use of customer password recovery tools such as GrabFF.
• Use of open-source network scanning tools like SoftPerfect.
• Use of free browsers including s3browser and Cent browser.
Although there seems to be some overlap, this does not confirm that Yanluowang was developed by, or in any way connected to Thieflock but it might mean that these attacks are being carried out by previous Thieflock affiliates who have moved to new organizations. We will have to wait and see how further attacks are carried out to get a good idea of who these attackers are and where they came from.